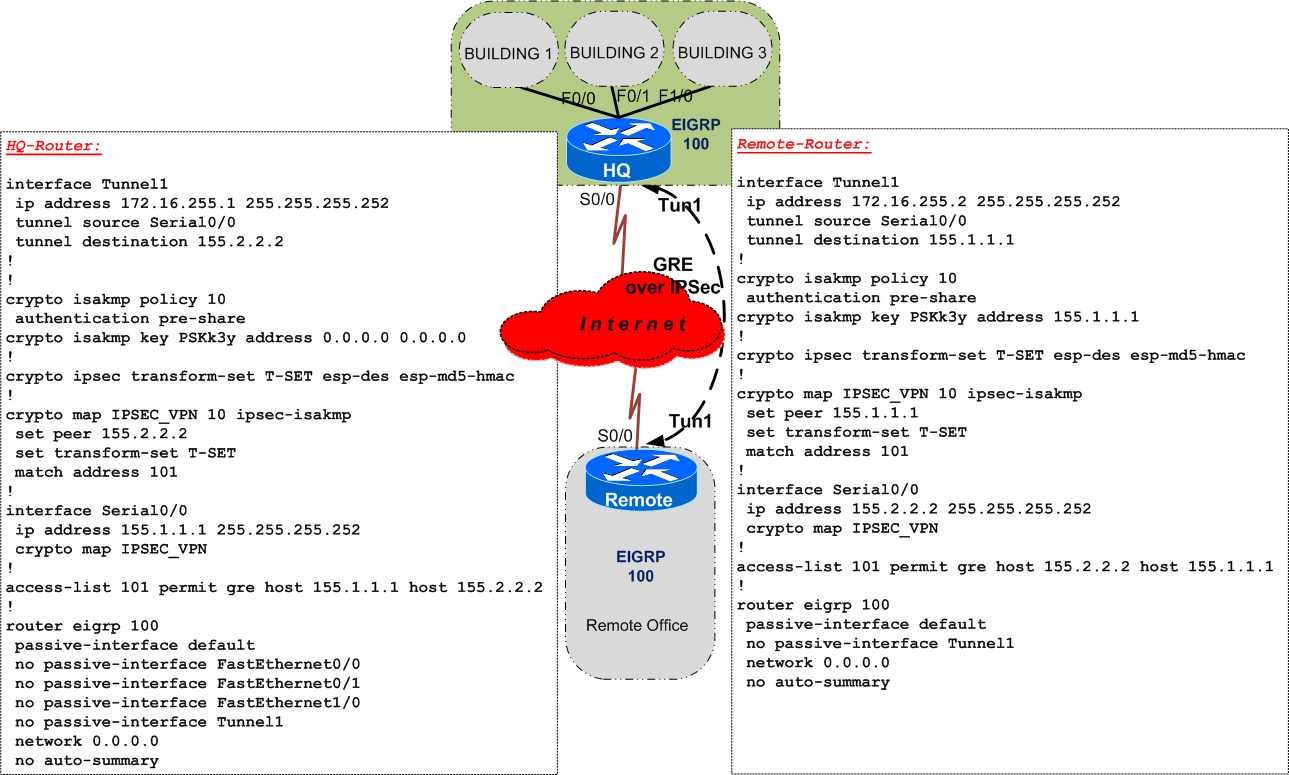
Your company is extending their network by opening a new Remote Office in a different city. In the HeadQuarters, you run EIGRP between buildings and the design team has decided to add the Remote Office into the EIGRP domain and to maintain the same level of protection/privacy over the Internet.
To achieve this you must configure an IPsec tunnel and run EIGRP over it - you've chosen to use the old method of crypto maps with a GRE tunnel that allows you to run dynamic routing protocols over IPsec.
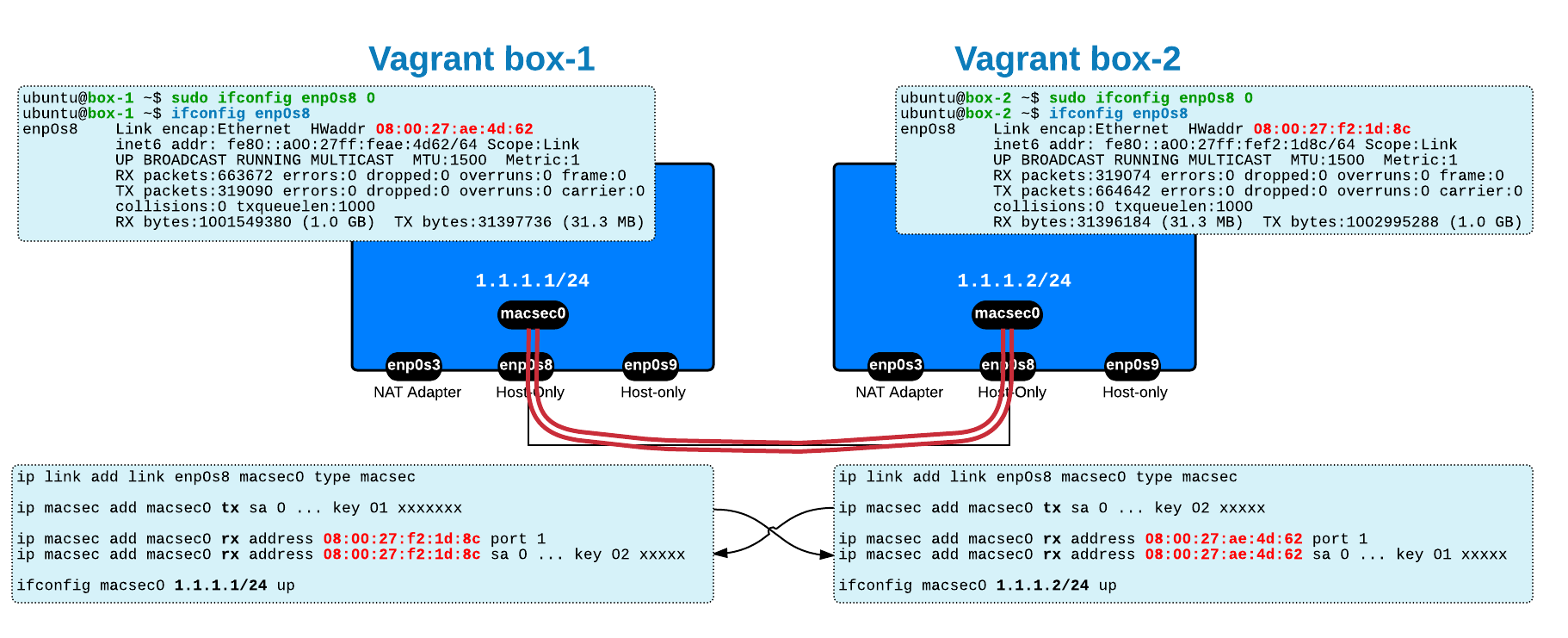
You perform the configuration below:
and you see that you have a successfull IPsec tunnel between HQ and Remote Office and the EIGRP peering is also UP:
HQ-Router#ping 172.16.255.2 Sending 5, 100-byte ICMP Echos to 172.16.255.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 52/76/100 ms HQ-Router# HQ-Router#sh crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id slot status155.1.1.1 155.2.2.2 QM_IDLE 1001 0 ACTIVE HQ-Router# HQ-Router#sh crypto ipsec sa local ident (addr/mask/prot/port): (155.1.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (155.2.2.2/255.255.255.255/47/0) ...#pkts encaps: 9, #pkts encrypt: 9 , #pkts digest: 9#pkts decaps: 8, #pkts decrypt: 8 , #pkts verify: 8 ... HQ-Router# *Mar 1 01:35:27.435: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 100:Neighbor 172.16.255.2 (Tunnel1) is up: new adjacency HQ-Router# HQ-Router#sh ip ei nei IP-EIGRP neighbors for process 100 H Address Interface Hold Uptime SRTT RTO Q Seq (sec) (ms) Cnt Num3 172.16.255.2 Tu1 14 00:00:06 84 5000 0 29 2 172.16.3.2 Fa1/0 10 00:05:49 52 312 0 120 1 172.16.2.2 Fa0/1 13 00:05:51 53 318 0 119 0 172.16.1.2 Fa0/0 11 00:05:53 50 300 0 121 HQ-Router#
After a while, you are aproached by the NOC telling you that the new IPsec tunnel and the EIGRP neighborship keep flapping up and down, impacting the connectivity between HQ and the remote office.
What is the problem ?
Post your answer in the ‘Comments’ section below and subscribe to this blog to get the detailed solution and more interesting quizzes.

 Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.
Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.

Comments
comments powered by Disqus