This post represents the solution and explanation for quiz-9.
Have a look at the quiz to understand the problem.
The quiz brings up for discussion a well-known problem of BGP peering over a firewall (in this case, a Cisco ASA), problem that is caused by two things: BGP uses TCP Options to perform authentication and the fact that firewalls do not "like" IP nor TCP OPTIONS.
As regards to the
- forwarded unchanged, for example: selective ACK, window scale, MSS, etc
- modified and then forwarded, for example in case of MSS clamping
- stripped off (actually, replace with NOP TCP Option, that is more like padding), for example: BGP MD5 TCP Option
- drop them (if they are not known and/or based on firewall configuration)
BGP controls most of the Internet traffic so it is very important to keep it secure. Besides the attacks against the routing protocol itself, BGP shares the same weaknesses as any TCP established application and is vulnerable to:
attacks against confidentiality - capture the TCP communication between two devices and learn the information exchanged ("eavesdropping")attacks against integrity - insert forged BGP messages into the BGP peering of two devices ("man in the middle")attacks agains the TCP session :- reset the TCP session by falsely terminating the BGP established connection (send a packet with a RST bit set or a packet with SYN bit set, while spoofing all the other fields of the already established connection)
- turn up a TCP session with an unauthorized party
- re-routing or looping the connectivity between the BGP peerings (in case of multihop BGP)
denial of service (DOS) attacks :- send a large number of SYN packets to consume device's memory - SYN flooding
- saturate the link so that the BGP will time out
There are more methods to protect against these attacks, but today we will only cover
This BGP MD5
- session hijacking and replay attacks (see above integrity attacks)
- unauthorized BGP session turn-ups
but it
- confidentiality - there's no encryption of the packet
- denial of service - as the router's CPU needs to perform MD5 hashing against all packets sent by attacker
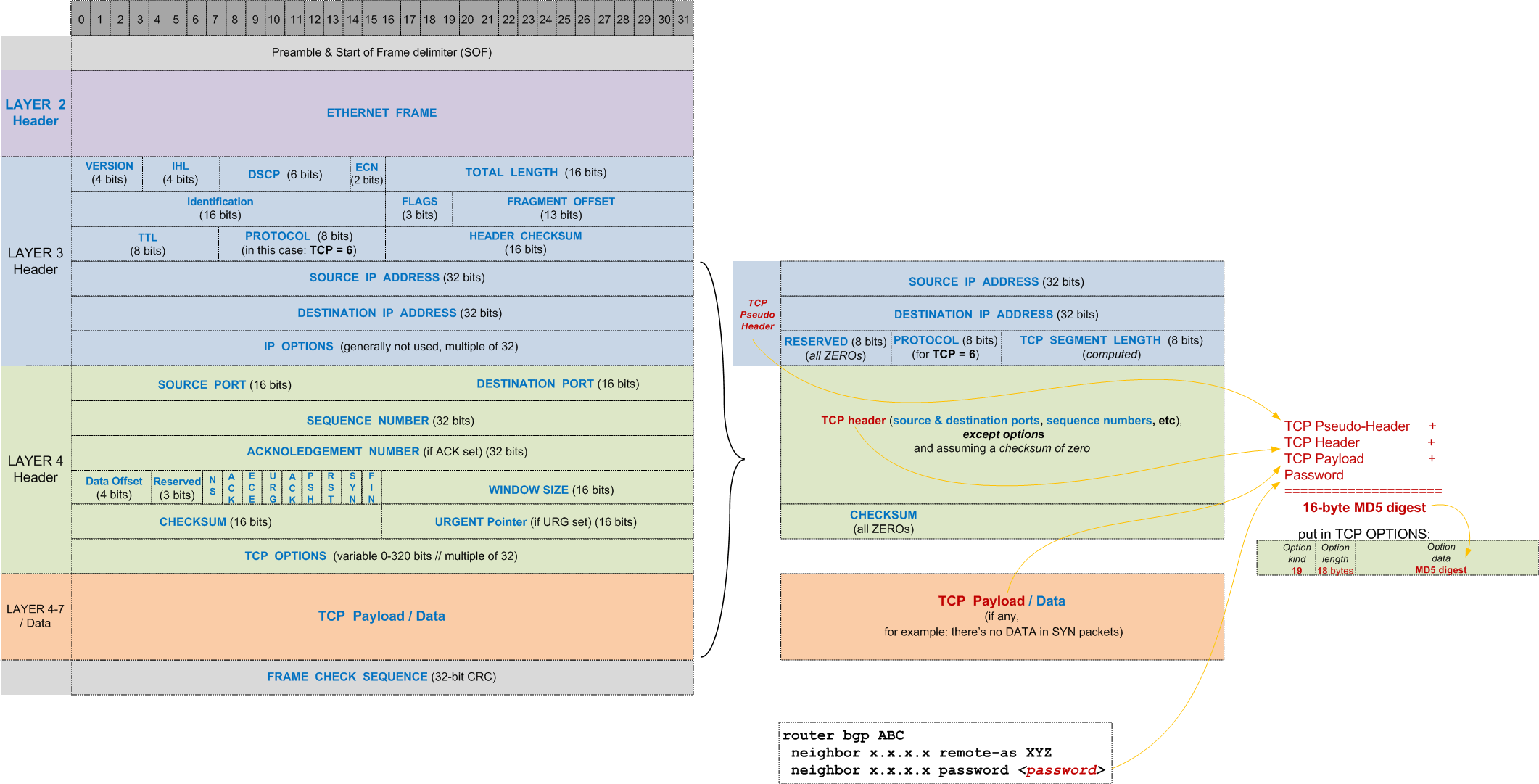
According to the RFC, the MD5 digest is performed against several fields from both the IP and TCP header, as shown in the following diagram:
- the
TCP Pseudo-Header (includes: IP source, IP destination, zero-padded protocol number and TCP segment length)- The pseudo-header is called like that because it refers to some fields from Layer 3/IP header
- the
TCP Header excluding options (includes: source port, destination port, sequence numbers, etc) - the TCP segment
data (if any) - the neighbor configured
password
Cisco PIX/ASA version 7.x and later has some default protections that impacts the BGP MD5 authentication. By default, Cisco ASA will:
-
-
The BGP MD5 digest needs to match on each side and for this to happen, the information used for hashing needs to be identical, such as: IP source and destination, source and destination port, sequence numbers, TCP segment data, password, etc...
Solution
For an authenticated BGP session to get established, it is not enough to allow TCP port 179 via the firewall but also you need to disable the above mentioned protections:
- disable TCP MD5 option rewriting
- disable TCP sequence number randomization
This also means, that it's not possible to perform NAT between BGP peers that uses authentication !
In the end, let's see how the configuration looks like on a Cisco ASA to allow the routers to have a successful BGP authenticated session:
FIREWALL# ! access-list ACL_BGP extended permit tcp any any eq bgp access-list ACL_BGP extended permit tcp any eq bgp any !tcp-map TCP_MAP_ALLOW_OPTIONS tcp-options range 19 19 allow ! class-map BGP_MD5 match access-list ACL_BGP ! policy-map global_policy class BGP_MD5set connection random-sequence-number disable set connection advanced-options TCP_MAP_ALLOW_OPTIONS ! service-policy global_policy global !
Thank you for your comments in the quiz!

 Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.
Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.

Comments
comments powered by Disqus