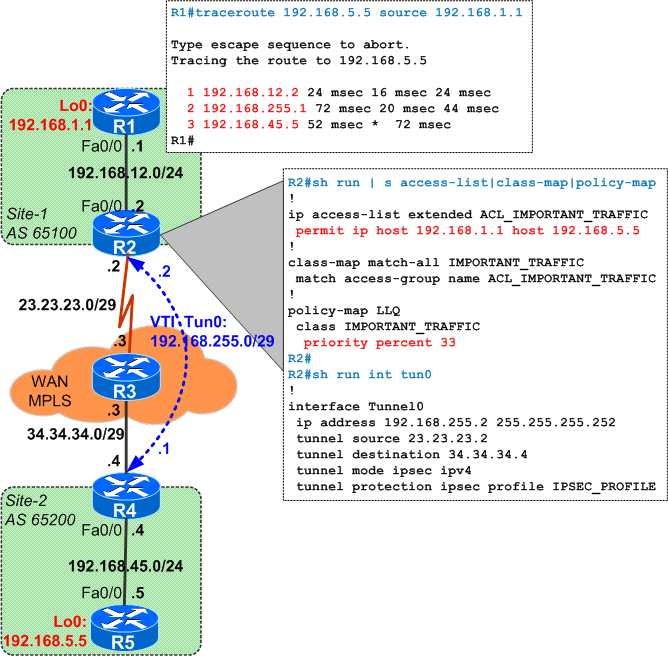
Company ABC runs a static VTI-based VPN tunnel between Site-1, hosting 192.168.1.1, and Site-2, hosting 192.168.5.5.
BGP is configured between the two sites, over the VTI Tunnel, making all traffic between the sites to be encrypted/protected by IPsec.
A new requirement is received from the customer, asking that all traffic from 192.168.1.1 (in Site-1) to 192.168.2.2 (in Site-2) must be prioritized. The network engineer creates the configuration below (access-list, class-map IMPORTANT_TRAFFIC and policy-map LLQ) as shown below:
What is missing to finish this task ?
DEVICES' CONFIGURATIONS:
hostname R1
!
no aaa new-model
ip cef
!
interface Loopback0
ip address 192.168.1.1 255.255.255.255
!
interface FastEthernet0/0
ip address 192.168.12.1 255.255.255.0
speed 100
full-duplex
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
router ospf 1
log-adjacency-changes
network 192.168.0.0 0.0.255.255 area 0
!
hostname R2
!
no aaa new-model
ip cef
!
class-map match-all IMPORTANT_TRAFFIC
match access-group name ACL_IMPORTANT_TRAFFIC
!
!
policy-map LLQ
class IMPORTANT_TRAFFIC
priority percent 33
!
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set TSET esp-3des esp-md5-hmac
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TSET
!
!
interface Tunnel0
ip address 192.168.255.2 255.255.255.252
tunnel source 23.23.23.2
tunnel destination 34.34.34.4
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
!
interface FastEthernet0/0
ip address 192.168.12.2 255.255.255.0
speed 100
full-duplex
!
interface Serial0/0
ip address 23.23.23.2 255.255.255.248
clock rate 2000000
!
!
router ospf 1
log-adjacency-changes
network 192.168.12.2 0.0.0.0 area 0
default-information originate
!
router bgp 65200
no synchronization
bgp log-neighbor-changes
redistribute connected route-map INTERNAL_INTERFACES
redistribute ospf 1
neighbor 192.168.255.1 remote-as 65100
no auto-summary
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 23.23.23.3
!
!
ip access-list extended ACL_IMPORTANT_TRAFFIC
permit ip host 192.168.1.1 host 192.168.5.5
!
!
route-map INTERNAL_INTERFACES permit 10
match interface FastEthernet0/0
!
hostname R3
!
no aaa new-model
ip cef
!
!
interface FastEthernet0/0
ip address 34.34.34.3 255.255.255.248
speed 100
full-duplex
!
interface Serial0/0
ip address 23.23.23.3 255.255.255.248
clock rate 2000000
!
!
hostname R4
!
no aaa new-model
ip cef
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set TSET esp-3des esp-md5-hmac
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TSET
!
!
interface Tunnel0
ip address 192.168.255.1 255.255.255.252
tunnel source 34.34.34.4
tunnel destination 23.23.23.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
!
interface FastEthernet0/0
ip address 34.34.34.4 255.255.255.248
speed 100
full-duplex
!
interface FastEthernet0/1
ip address 192.168.45.4 255.255.255.0
speed 100
full-duplex
!
router ospf 1
log-adjacency-changes
network 192.168.45.4 0.0.0.0 area 0
default-information originate
!
router bgp 65100
no synchronization
bgp log-neighbor-changes
redistribute connected route-map INTERNAL_INTERFACES
redistribute ospf 1
neighbor 192.168.255.2 remote-as 65200
no auto-summary
!
ip route 0.0.0.0 0.0.0.0 34.34.34.3
!
!
route-map INTERNAL_INTERFACES permit 10
match interface FastEthernet0/1
!
!
hostname R5
!
!
no aaa new-model
ip cef
!
!
!
!
interface Loopback0
ip address 192.168.5.5 255.255.255.255
!
interface FastEthernet0/0
ip address 192.168.45.5 255.255.255.0
speed 100
full-duplex
!
router ospf 1
log-adjacency-changes
network 192.168.0.0 0.0.255.255 area 0
!
Post your answer in the 'Comments' section below and subscribe to this blog to get the detailed solution and more interesting quizzes.

 Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.
Costi is a network and security engineer with over 10 years of experience in multi-vendor environments. He holds a CCIE Routing and Switching certification and is currently pursuing same expert-level certifications in other areas. He believes that the best way to learn and understand networking topics is to challenge yourself to fix different problems, production-wise or lab-type exams. He also enjoys teaching networking and security technologies, whevever there is an opportunity for it.

Comments
comments powered by Disqus